For the past decade, K–12 districts have focused on solving the access problem, using tools like single sign-on (SSO), automated rostering, and identity management systems to simplify digital learning access while attempting to protect student data privacy in K–12. These tools have transformed how quickly teachers and students can get into digital tools.
Those efforts worked. Access is no longer the bottleneck.
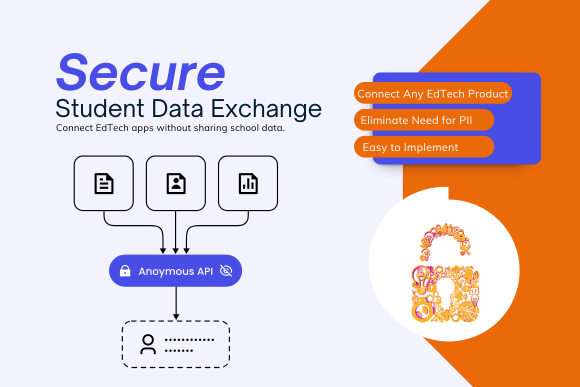
But that success has created a new challenge: student data now moves into more systems, more often, and with less visibility than ever before. Secure student data exchange can no longer be defined by who can log in. It must be defined by what data is shared, for what purpose, and for how long, and increasingly, by whether full identities are shared at all.
This is why districts have started the shift from identity and access management (IAM) in K–12 to a zero-trust data architecture like ecosystem orchestration, and from there toward self-sovereign data principles built on tokenization of student data and selective disclosure.
Data Governance for School Districts: SSO Is the Baseline, Not the Strategy
In most districts today, SSO and rostering are expected. Teachers assume their apps will be ready on day one, with classes pre-populated and logins handled behind the scenes. Manual account creation and CSV uploads have largely disappeared, replaced by automated syncs that improve efficiency and reduce errors.
The unintended outcome is that more systems than ever now hold student data. Each new application connected to the same identity and roster feeds inherits a broad slice of student information, often far more than it truly needs.
SSO solves authentication. Rostering solves provisioning. Neither was designed to govern student data privacy in K–12.
Why Access Alone Is Not a Privacy Strategy
When access infrastructure becomes the default gateway to every new tool, districts can unknowingly create environments where data flows faster than governance can keep up.
Common warning signs include:
- No authoritative inventory of applications receiving student data
- Data privacy agreements reviewed after tools are already in use
- Difficulty answering basic questions such as where data is stored, what attributes are shared, or who still has access
Ironically, many districts now have less clarity than they did in the manual era, despite far more sophisticated systems.
The issue isn’t interoperability. It’s uncontrolled interoperability.
Introducing Ecosystem Orchestration for Better Student Data Privacy
To move beyond “connect everything and hope for the best,” districts need a layer above SSO and rostering that governs secure student data exchange across the ecosystem.
This is a zero-trust data architecture framework called ecosystem orchestration: a policy‑driven control plane that determines what data moves between systems, under what conditions, and for how long.
In practical terms, ecosystem orchestration is a governance approach to secure student data exchange that prioritizes tokenization, data minimization, and policy-based controls over broad identity sharing.
At its core, zero-trust ecosystem orchestration reframes integrations from identity sharing to data minimization and tokenization.
Key characteristics of data governance for school districts include:
Policy-first design – Data flows are governed by explicit rules, not just technical capability.
Zero‑trust – No application is implicitly trusted with full student records.
Tokenized exchange – Systems receive tokens, attributes, or derived claims instead of raw personally identifiable information whenever possible.
Rather than sending full identity profiles to every vendor, districts issue purpose‑limited proofs such as:
“This student is currently enrolled in Grade 7.”
“This user belongs to School A and has teacher role permissions.”
These claims can be time‑bound, scoped, and revoked, aligning closely with self‑sovereign data principles without requiring districts to overhaul their entire infrastructure.
Tokenization of Student Data as the Bridge to Self‑Sovereign Data
Self‑sovereign identity is often discussed as a future possibility, but districts can begin adopting self-sovereign data principles today through tokenization.
Tokenization strengthens student data privacy in K–12 by replacing persistent identifiers with non-reversible tokens that are meaningful only within a defined context. If a system doesn’t need a student’s name, ID number, or birthdate, it shouldn’t receive them.
In practice, this means:
- Applications authenticate users via SSO but receive no stored identity data.
- Rostering exchanges use pseudonymous identifiers instead of district‑wide student IDs.
- Analytics and reporting rely on derived attributes rather than raw records.
Each step reduces risk while preserving functionality and keeps authority over data firmly with the district.
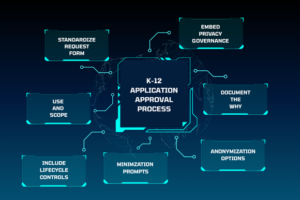
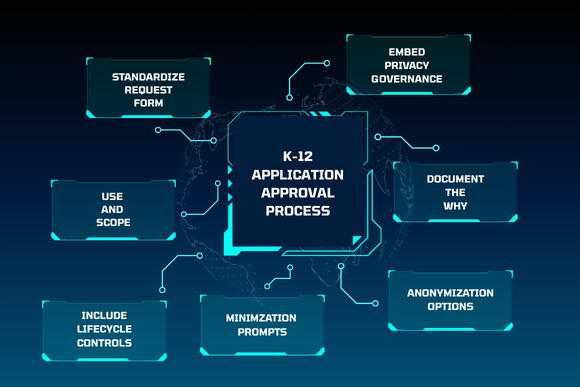
What a Governed Ecosystem Looks Like
In an orchestrated environment, new tools follow a defined lifecycle instead of jumping straight into full data feeds.
1. App intake and justification
Requests capture instructional purpose, target users, and explicit data requirements. Intake itself becomes an act of data minimization.
2. Risk and data scope review
Security posture, data residency, and contractual protections are evaluated before integration, not after.
3. Controlled provisioning
Approved applications are connected through SSO and rostering, but only within the boundaries defined by policy. Tokens and scoped attributes replace full records wherever possible.
4. Ongoing monitoring
Usage, incidents, and access patterns are reviewed against expectations, allowing data scopes to be refined and tightened without dismantling the integration.
5. Decommissioning and revocation
When a tool is retired, tokens are invalidated, data flows are shut off, and contractual data deletion requirements are enforced.
At every stage, the district retains visibility and control.
A Simple Maturity Model
Districts typically move through four stages:
Level 1 – Manual and fragmented
Level 2 – Connected access (SSO and rostering)
Level 3 – Interoperable but under‑governed
Level 4 – Governed ecosystem orchestration
Level 4 reflects a shift toward self‑sovereign‑inspired posture: systems receive only what they need, access is centrally governed, and data authority remains with the district.
Data Governance for School Districts: From Access to Control
The path forward doesn’t require abandoning existing systems. It requires reframing how they are used.
Practical first steps include:
- Creating a living inventory of applications and data flows.
- Strengthening app intake with explicit data justification.
- Defining policies for the tokenization of student data and minimal data exchange.
- Piloting zero‑PII integrations where possible.
- Establishing a cross‑functional governance forum.
Each step moves districts closer to self-sovereign data principles and a future where secure student data exchange is not about who can log in but about who controls the data, how it is shared, and when it can be taken back.
That is the promise of zero-trust ecosystem orchestration, and the foundation of truly modern student data privacy, one built on secure student data exchange, tokenization of student data, zero-trust architecture, and self-sovereign-inspired data governance for K–12 districts.