School districts are under constant attack, from ransomware and phishing to vendor breaches and AI-driven data leaks. Between July 2023 and December 2024, 82% of K-12 schools experienced a cybersecurity incident. With back to school just around the corner, K-12 cybersecurity is more than a passing thought–it is the primary mandate for all schools.
How K-12 IT Leaders Can Stay Ahead of Cyber Threats This Fall
K-12 IT leaders are under so much pressure in today’s education environment. They are responsible for device distribution and management, school IT infrastructure, and defending their networks against increasingly sophisticated cyberattacks.
Yet despite the growing complexity of these threats, IT teams are still expected to manage everything with limited staff and resources.
As school cybersecurity shifts from an IT responsibility to a district-wide priority, here’s what K-12 IT leaders should focus on to protect student data and keep learning on track in 2025, and how forward-thinking districts are reimagining their cybersecurity strategies.
The State of K-12 Cybersecurity in 2025
K-12 schools store vast amounts of valuable data, which makes them prime targets for cybercriminals. Unfortunately, schools also have some of the least protected infrastructure.
- 82% of K-12 schools have experienced a cyberattack in the past 18 months
- 55 % of school cyberattacks originate from third-party vendors, reports K12 SIX, a nonprofit threat intelligence community for U.S. K-12 education.
- Just one person or a small IT team often manages a district’s ed-tech apps and integrations, but what used to be a manageable 20-25 apps has skyrocketed to more than 1,300 apps, with many of them unsanctioned.
- Phishing scams are the biggest perceived threat amongst edtech leaders, according to a CoSN survey.
- Microsoft reported that “quishing,” a new phishing technique using QR codes, is on the rise. Phishing and quishing account for 45% of cybersecurity incidents in schools.
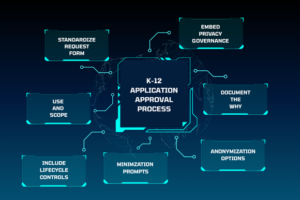
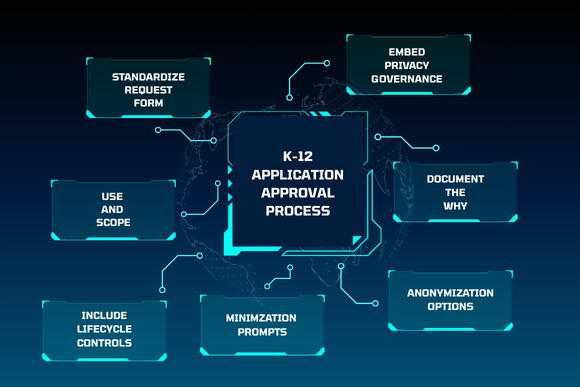
- Governance is getting more complex. States are tightening privacy laws. Similar to the 2016 Student Online Personal Protection Act (SOPPA) established in Illinois, New York has established a new law that protects students’ personally identifiable information (PII) from unauthorized disclosure and gives parents more rights about PII. We can expect these laws to continue to proliferate, especially after the PowerSchool breach.
Top 5 Cyber Threats Facing School Districts This Year
School districts have always been a target for cybercriminals, but the stakes are higher than ever in 2025. With rapid adoption of new technology, a growing reliance on cloud-based tools, and the increasing sophistication of attackers, IT leaders are juggling more risks and more endpoints than ever before. Protecting student data now means looking beyond your own network to the entire ecosystem of vendors, apps, devices, and AI tools connected to it. Here are five areas to keep on your radar this year, along with practical ways to reduce exposure.
1. Unsecured EdTech Integrations
From learning management systems to digital reading platforms, most districts now rely on hundreds, if not thousands, of apps. But every integration is a potential access point for cyberattacks. If even one vendor is misconfigured, fails to comply with privacy laws, or doesn’t meet your district’s security standards, student data could be exposed. The challenge isn’t just the volume; it’s the pace at which new tools are adopted. Building a process for vetting, monitoring, and deactivating apps is essential to reducing risk.
2. Phishing and Credential Theft
Attackers know that busy seasons like back-to-school time are when staff and faculty are most likely to click before thinking. Back-to-school phishing emails often impersonate HR, IT support, or district leadership to trick recipients into sharing passwords or downloading malicious attachments. Ongoing, scenario-based training for staff can make a substantial difference in spotting these attempts before they succeed.
3. Unpatched Devices and BYOD
A single outdated Chromebook, tablet, or teacher laptop can become the entry point for ransomware or spyware. In districts that allow bring-your-own-device (BYOD), the risk multiplies, especially when personal devices bypass district monitoring. Setting clear device compliance rules, automating updates where possible, and routinely scanning for vulnerabilities helps close this gap.
4. Vendor Breaches and Shadow IT
Even if your district’s systems are secure, your vendors’ systems may not be. A breach at a service provider can still compromise your data, and without centralized oversight, districts often don’t know until it’s too late. Shadow IT, when staff adopt unapproved apps, adds another blind spot. Consolidating logins, monitoring vendor access, and using secure integration tools can improve visibility and reduce exposure.
5. AI-Powered Data Scraping and Leakage
Generative AI tools are finding their way into classrooms, lesson planning, and administrative work, but many are designed to collect and store user inputs. Without strict settings and clear policies, sensitive information about students or staff can end up in third-party databases. Work closely with curriculum and teaching teams to approve safe AI tools and establish rules for what can and can’t be used.
Back-to-School Cybersecurity Checklist for K-12 IT Leaders
1. Secure Your EdTech Integrations
☐ Maintain a live inventory of all connected apps
☐ Remove unused or unapproved tools
☐ Establish a vetting process for new integrations
2. Strengthen Defenses Against Phishing & Credential Theft
☐ Conduct regular, safe phishing simulations
☐ Provide ongoing, scenario-based staff training
☐ Set up multi-factor authentication (MFA) for critical systems
3. Close Device Security Gaps
☐ Require minimum security standards for all devices, including BYOD
☐ Automate updates on district-issued devices
☐ Schedule routine vulnerability scans
4. Monitor Vendors & Eliminate Shadow IT
☐ Centralize vendor management and app approvals
☐ Monitor all third-party connections through one platform
☐ Disable access for vendors who no longer meet security standards
5. Control AI Tool Use & Data Sharing
☐ Vet all AI tools for privacy compliance before classroom use
☐ Set clear rules for what data can be entered into AI systems
☐ Provide staff guidance on safe, approved AI practices
What Leading Districts Are Doing Differently
K-12 leaders know that protecting student data takes more than reacting to threats—it requires building security into every connection. Forward-thinking districts are:
- Centralizing control over all app integrations
- Automating enforcement of privacy policies and access permissions
- Standardizing vendor onboarding to reduce risk at the source
- Monitoring all data activity in real time
The result: greater visibility, fewer blind spots, and stronger protection for student data—without any added complexity for IT teams.
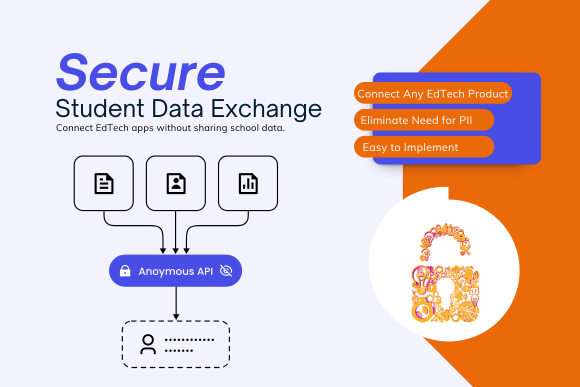
SchoolDay: A Smarter Way to Secure Student Data
When one IT admin might be managing over a thousand apps, the answer isn’t doing more—it’s working smarter. SchoolDay’s ecosystem orchestration platform empowers IT teams to securely manage data exchange without increasing workload.
- Manage app integrations centrally
- Automate privacy compliance
- Monitor data activity in real time
School IT leaders don’t need to do more; they need smarter ways to manage their digital ecosystem—and keep student data safe.